With cyberattacks and cybersecurity incidents rising, investors want to know whether their assets are protected and safe and whether their investments are secured from cyberattacks.
On July 26, 2023, the US SEC adopted new rules to enhance and standardize disclosures regarding cybersecurity risk management, strategy, governance, and incidents of public companies subject to the Securities Exchange Act of 1934 (“Exchange Act”). With the new rule, organizations need to be involved in managing their cyber risks, be familiar with how they should manage them, and be responsible for providing relevant and useful information.
Although not obliged by SEC guidance from 2011 and 2018, many public companies are already providing cybersecurity disclosures. However, both companies and investors, would benefit more from more consistent and comparable disclosures, making them more effective for decision-making.
Who is affected?
Under the new rules, all types of SEC filers are affected, including domestic registrants, Foreign Private Issuers (“FPIs”), Smaller Reporting Companies (“SRCs”), and Emerging Growth Companies (“EGCs”).
Main Provision
The new rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure have two components:
1. Disclosures of material cybersecurity incidents
2. Annual disclosure of cybersecurity risk management, strategy, and governance.
Both cybersecurity disclosures need to be presented in Inline eXtensible Business Reporting Language (“Inline XBRL”), as required by the new rules.
Disclosures on Material Cybersecurity Incidents
Under the new rules, Item 1.05 is added to Form 8-K, which requires domestic registrants to disclose the following information regarding a material cybersecurity incident:
1. Material aspects of its nature, scope, and timing
2. Material impact or reasonably likely material impact on the registrant, including the registrant’s financial condition and results of operations.
Under SEC cybersecurity rules, a material incident is an event which is substantially likely to be important to a reasonable investor when making an investment decision. There is no specific financial threshold to consider a cyber incident as material, as it requires an analysis of both quantitative and qualitative information related to the incident.
Any material cybersecurity incident must be filed within four (4) business days of determining an incident was material. It is important to note that the filing is tied not to the discovery of the incident but to the determination that it is material. Registrants should determine whether an incident is material or not without unreasonable delay; however, a registrant may delay filing if the United States Attorney General determines immediate disclosure would pose a substantial risk to national security or public safety.
It is worth noting that a registrant is not required to include specific or technical information in its disclosures that could affect its incident response, remediation or reveal potential system vulnerabilities.
For FPIs, disclosure must be made on Form 6-K promptly after the incident is disclosed or otherwise publicized in a foreign jurisdiction to any stock exchange or security holders.
Annual Disclosure of Cybersecurity Risk Management, Strategy, and Governance
Companies must now disclose details about their cybersecurity defenses in their annual reports. The new rules introduce Item 106 to Regulation S-K, which mandates disclosures of certain information on cyber risk management, strategy, and governance within Form 10-K filings. FPIs also have a comparable disclosure requirement in their annual reports in, Item 16K which has been added Form 20-F.
Risk Management and Strategy
Under Regulation S-K Item 106(b) – Risk Management and Strategy, registrants are required to describe their processes, if any, for the assessment, identification, and management of material risks from cybersecurity threats. They must also describe whether any risks from cybersecurity threats have materially affected or are reasonably likely to materially affect their business strategy, results of operations, or financial condition. The following are the elements that a registrant should address in its Item 106(b) disclosure, as applicable:
• Whether and how the described cybersecurity processes in Item 106(b) have been integrated into the registrant’s overall risk management system or processes
• Whether the registrant engages assessors, consultants, auditors, or other third parties in connection with any such processes
• Whether the registrant has processes to oversee and identify material risks from cybersecurity threats associated with using any third-party service provider
With these specific disclosure requirements, registrants are expected to:
1. Identify the methods used by the company in identifying and assessing risks, which should ideally cover incidents involving data theft and business continuity events.
2. Consider addressing residual risks and identifying how the company designs or updates its cybersecurity processes after risk assessment.
3. Consider evaluating the effectiveness of the company’s controls and safeguards, including any oversight and assessment of third parties used in the process.
The list is not exhaustive, and the registrants should consider disclosing other information that is deemed relevant and necessary.
Governance
Under Item 106(c) – Governance, registrants are required to describe the board’s oversight of cybersecurity threats and management’s role in assessing and managing material risks from cybersecurity threats. The disclosure must include:
• Whether and which management positions or committees are responsible for assessing and managing such risks, and the relevant expertise of such persons or members in such detail as necessary to fully describe the nature of the expertise
• The processes by which such persons or committees are informed about and monitor the prevention, detection, mitigation, and remediation of cybersecurity incidents
• Whether such persons or committees report information about such risks to the Board of Directors or a committee or subcommittee of the Board of Directors
The requirements for FPIs on their Form 20-F are the same as those of Regulation S-K Item 106(c) mentioned above.
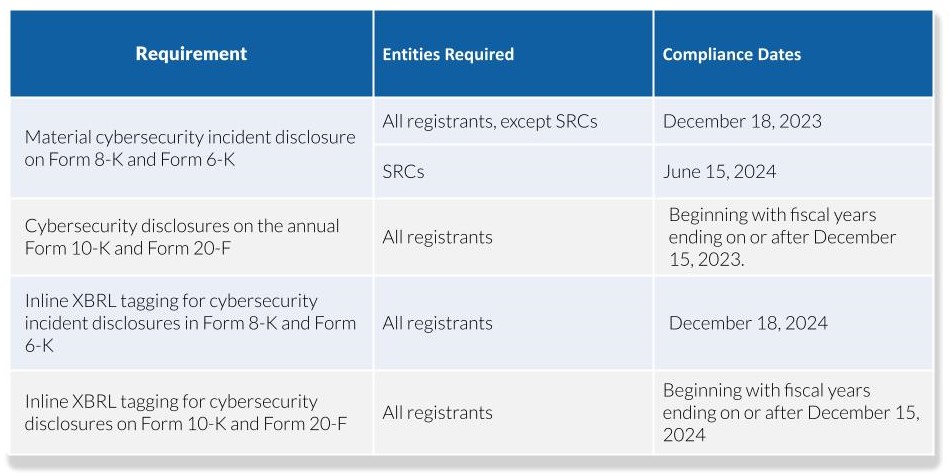
Compliance Dates
Although the new rules directly impact public companies, private companies are also encouraged to follow these requirement. Some private companies have been charged to disclose the names of clients whose information may have been exposed to cyberattacks and even pay penalties, with some paying over $200,000 to settle the charges. Even if the new rule is technically only applicable to public companies, all other organizations, including private entities, should familiarize themselves with the regulations. This also emphasizes that cybersecurity is everyone’s concern, not just because many private entities are third parties to public companies (which also makes them liable in case of cyber incidents), but because private companies also handle various data, are accountable to their investors, and need to protect their reputations.
It’s Time to Get Ready
There is no single approach to compliance with the new SEC cybersecurity disclosure rule that would address all the complexities and effects of risks. However, companies may use these guidelines to prepare for the new requirement:
1. Establish and understand each department’s role in compliance. This will ensure smooth communication and coordination between and among departments in case of a cybersecurity incident.
2. Ensure that the necessary processes are in place for determining, assessing, addressing, and reporting risks. This also includes regular risk assessments, response plans, and recovery plans.
3. Determine all parties to which the cybersecurity policies, procedures, and practices should be extended to, such as suppliers.
4. Assess and test the organization’s overall preparedness.
How Can Scrubbed Help You?
Cybersecurity risk management is one of the most crucial activities that organizations have to focus on to ensure that operations will run smoothly, protect sensitive data and information, and achieve business objectives. It also gives assurance to the shareholders and other investors on the safety of their investments.
Scrubbed provides a wide range of relevant services, including:
• Open-Source Intelligence (OSINT) Research Assistance
• Vulnerability Assessment and Penetration Testing (VAPT) Assistance
• Cybersecurity Framework Policy and Procedure Evaluation Support
• Preparation of Cybersecurity Disclosures under the new SEC rules
• Strategic financial oversight through fractional CFO services
At Scrubbed, we support companies including those in highly regulated industries like biotech, with a wide range of relevant services. Our biotech accounting services team works closely with cybersecurity experts to help safeguard sensitive financial and operational data. Contact Scrubbed, or email us at [email protected] to learn how the Risk Advisory Group, and the Technical Accounting Group, can assist you.
Disclaimer: The information contained herein is general and is not intended to address the circumstances of any particular individual or entity. It is not intended to be relied upon as accounting, tax, or other professional services. Please refer to your advisors for specific advice. Although we endeavor to provide accurate and timely information, there can be no guarantee that such information is accurate as of the date it is received or will continue to be accurate in the future. No one should act upon such information without appropriate professional advice after a thorough examination of the particular situation.
*Disclaimer: Services being offered do not require a state license.
**Special thanks to Lord Gen Rilloraza for his valuable contribution to this article.
References: https://www.sec.gov/files/rules/final/2023/33-11216.pdf # https://www.sec.gov/corpfin/secg-cybersecurity # https://www.sec.gov/news/statement/gensler-statement-cybersecurity-072623 # https://www.bitsight.com/blog/sec-regulations-what-material-cybersecurity-incident#:~:text=According%20to%20the%20SEC%20rules,for%20a%20material%20cyber%20incident. # https://www.schellman.com/blog/cybersecurity/how-to-prepare-for-sec-new-cyber-disclosure-rule # https://www.thomsonreuters.com/en-us/posts/government/sec-cybersecurity-rules/ # https://www.auditboard.com/blog/sec-cybersecurity-rules/ # https://www.troutman.com/insights/sec-charges-privately-held-monolith-resources-for-violating-whistleblower-protection-rules.html#:~:text=Monolith%20has%20also%20agreed%20to,penalty%20to%20settle%20the%20charges.&text=This%20enforcement%20action%20highlights%20that,companies%20with%20Rule%2021F%2D17. # https://www.law.com/nationallawjournal/2023/07/24/in-sec-battle-covington-ordered-to-disclose-names-of-7-clients/?slreturn=20231128013845 # https://www.bakerlaw.com/insights/addressing-the-secs-new-cybersecurity-risk-management-strategy-governance-and-incident-disclosure-requirements/








